In this article, we will configure the IPSec Tunnel between FortiGate & SonicWall Firewall. Both Firewalls are next-generation and have the capability of IPSec VPN. A basic understanding of the IPSec VPN will help configure the IPSec tunnel. So, let’s start.
How to configure IPSec tunnel between SonicWall Firewall & FortiGate Firewall
You must need static routable IP addresses across both devices. However, you can also use the FQDN of the devices. In this example, we will use the static routable IP addresses on both the devices. We will configure IPSec IKE Phase 1 & Phase 2. Before configuring the IPSec tunnel, let’s first discuss the lab setup for this article.
Scenario – IPSec tunnel between FortiGate Firewall & SonicWall Firewall
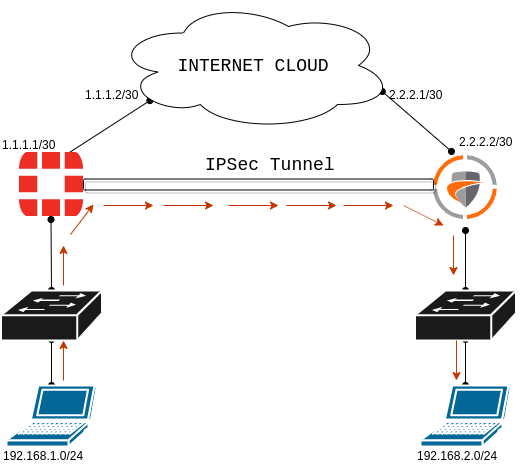
Both devices are connected to the Internet. On FortiGate Firewall, we are using two subnets. The Internet subnet is 1.1.1.0/30 & the LAN subnet is 192.168.1.0/24. On the SonicWall Firewall side, the Internet subnet is 2.2.2.0/30 and the LAN subnet is 192.168.2.0/24. Both devices have Internet connectivity. Before the configuration, make sure that both the devices are reachable from each other. You can refer to the below screenshot for better understanding.
Steps to configure IPSec Tunnel on SonicWall Firewall
First, we will configure the IPSec tunnel on the SonicWall Next-Gen Firewall. We need to configure Encryption & Authentication Methods, Key Life Time, and DH Group for both IKE Phases. Let’s start our configuration.
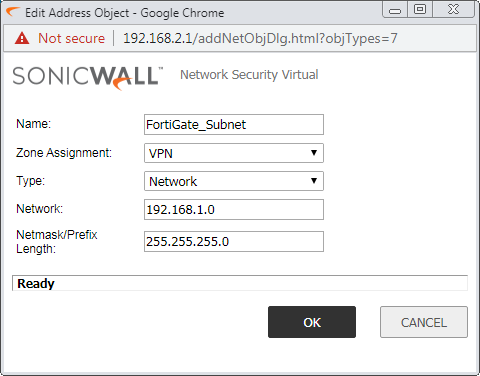
Step 1: Create the Network Address Object for IPSec Tunnel
First, we need to create the Network Object for the Destination Subnet, you want to access through the IPSec tunnel. In my case, my destination subnet is 192.168.1.0/24 which is connected to the FortiGate Side. Navigate to Network >> Address Object and click on Add. You can refer to the below image, to create an address object.
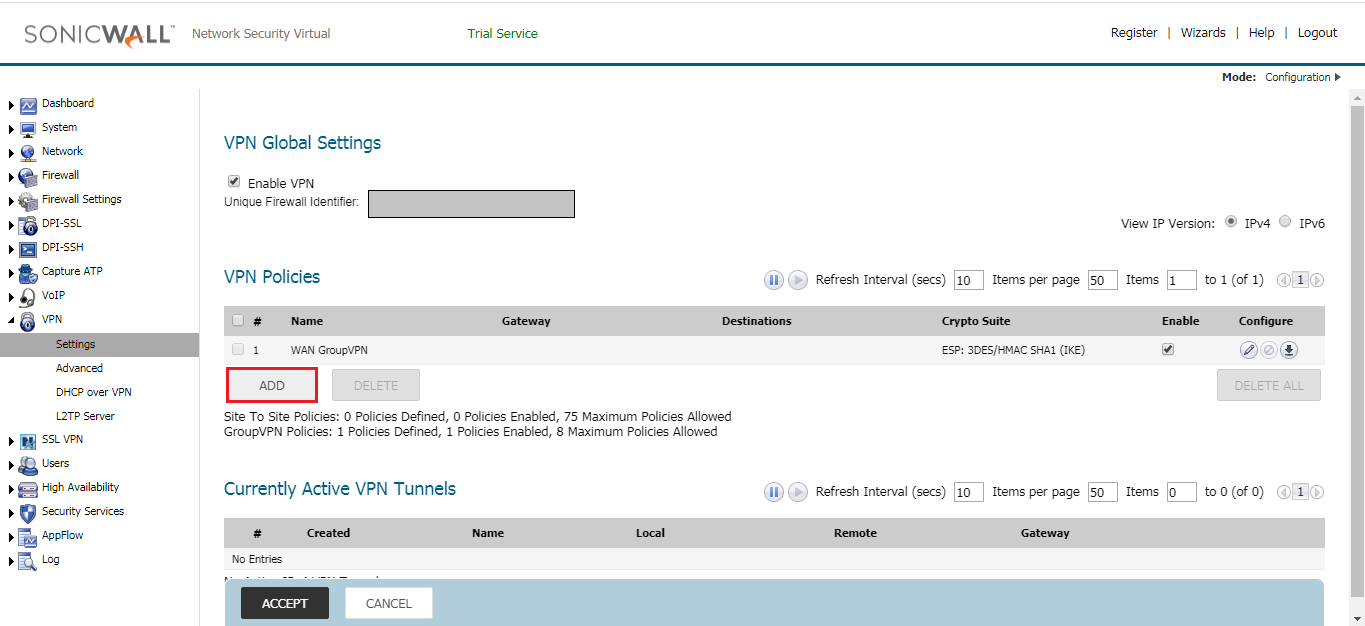
Step 2: Configuring the VPN Policies for IPSec Tunnel on the SonicWall Firewall
In this step, you need to define the VPN Policy for the IPSec tunnel. Here, you need to create a tunnel with Network, Phase 1 & Phase 2 parameter. Navigate to VPN >> Settings >> VPN Policies and click on Add. Once, you click on Add, and another pop-up window will open.
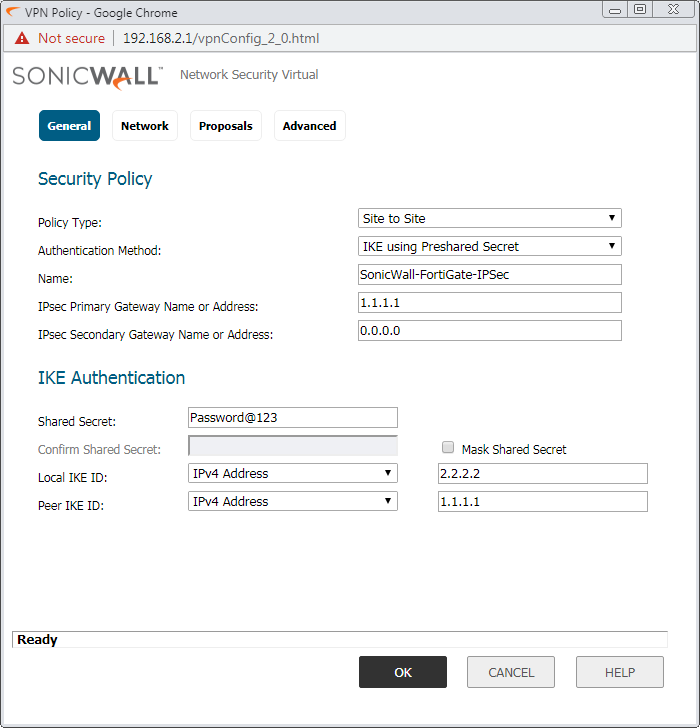
In the General tab, select the Policy Type: Site to Site and Authentication Method: IKE using Preshared Secret. In the Name field, give the name of IPSec Tunnel, i.e. SonicWall-FortiGate-IPSec. You can define primary and secondary Name/IP for the Gateway. In this example, I’ll use only the primary IP. So, the IPsec Primary Gateway Name or Address will be 1.1.1.1 i.e. FortiGate IP Address.
In IKE Authentication, provide the Pre-Shared key. This key must be the same on both the appliance. In Local & Peer IKE ID, give the public IP of SonicWall and FortiGate firewall respectively.
Access the Network tab, here you need to configure the Local and Remote Network. In this example, we want to access the LAN subnet of both sites. In the Local Network field, select the LAN Subnet. Now, in the Remote Network field, you need to define the Network Object we created in Step 1.
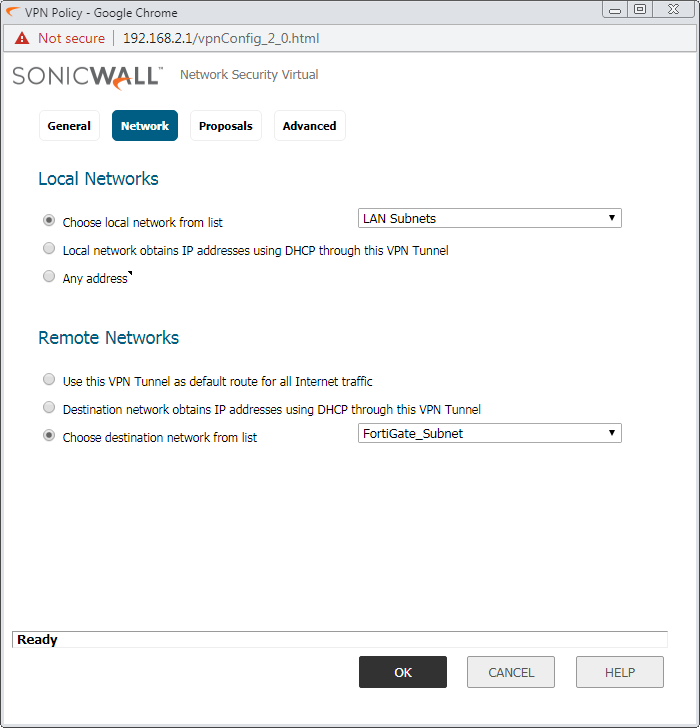
Access the Proposal tab, and configure the Encryption, Authentication, DH-Group, and Key-lifetime value.
Note: Make Sure, Encryption, Authentication, DH-Group & Key-Lifetime value must be the same on both the appliances.
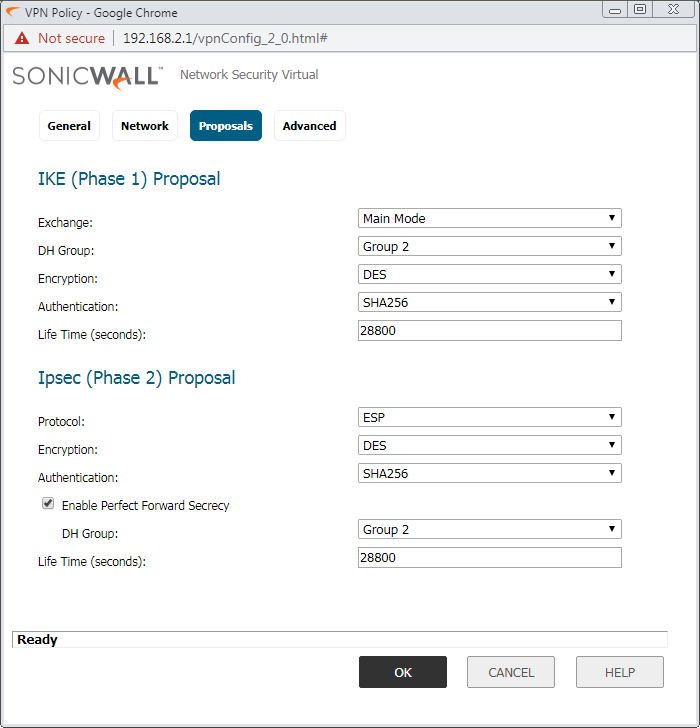
In the Advanced Tab, Enable the Keep-Alive. However, if you want to manage the SonicWall firewall over the IPSec tunnel, you need to select SSH/HTTPS in Management via the SA field. Refer to the below image for more the configuration.
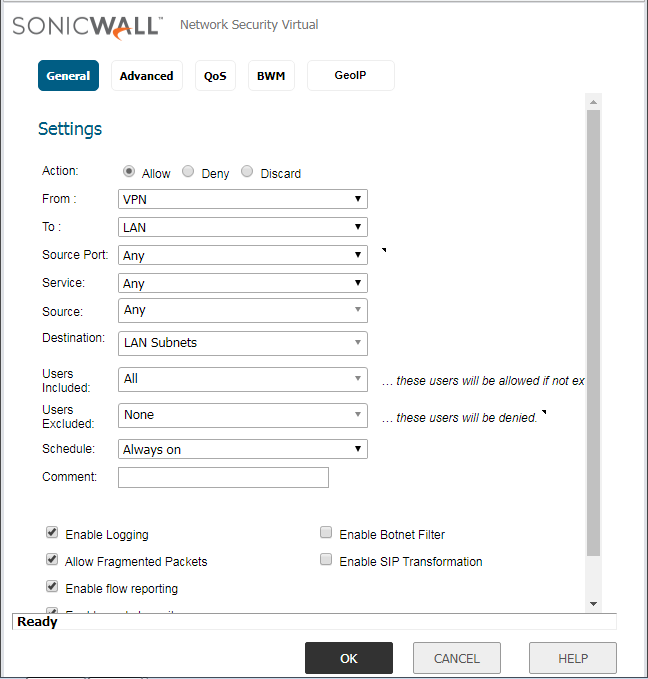
Step 3: Configuring the Access Rule for the IPSec Tunnel
By default, an access rule created, from LAN–VPN. However, for bi-directional communication, we need to create an additional rule on the SonicWall Firewall. Navigate to, Firewall >> Access Rules and click on Add. Add a policy from LAN–VPN. You need to define the services on the same policy. However, in this example, I’m using All Services. You can refer to the below image for the policy configuration.
We successfully configured the IPSec tunnel on SonicWall Firewall. In the next steps, we will configure IPSec tunnel on FortiGate firewall!
Steps to configure IPSec Tunnel in FortiGate Firewall
Now, we will configure the IPSec Tunnel in FortiGate Firewall. In this example, I’m using FortiGate Firmware 6.2.0. Although, the configuration of the IPSec tunnel is the same in other versions also. Just login in FortiGate firewall and follow the following steps:
Creating IPSec Tunnel in FortiGate Firewall – VPN Setup
Unlike the SonicWall Firewall, the FortiGate firewall gives you templates, which help you to create an IPSec tunnel by clicking Next Next, etc. Unfortunately, pre-defined templates are only available for Cisco ASA and FortiGate itself. Therefore, we need to create a custom tunnel. In order to create an IPSec tunnel with SonicWall, just log in to FortiGate Firewall, and locate VPN >> IPSec Tunnels >> Create New. In the VPN Setup tab, you need to provide a user-friendly Name. Now, In Template Type select Custom and click Next.
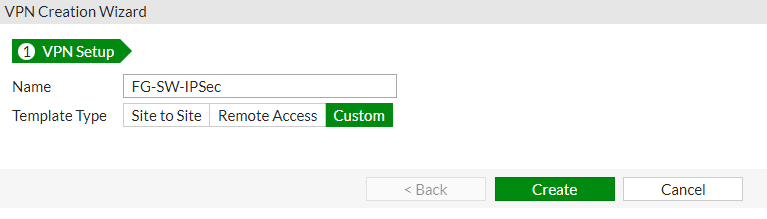
IPSec Tunnel in FortiGate – Phase 1 & Phase 2 configuration
Now, we will configure the Gateway settings in the FortiGate firewall. Select, IP Version IPv4/IPv6. In the Remote Gateway select Static IP Address & in Address field, give the remote site SonicWall Firewall Public IP i.e. 2.2.2.2.
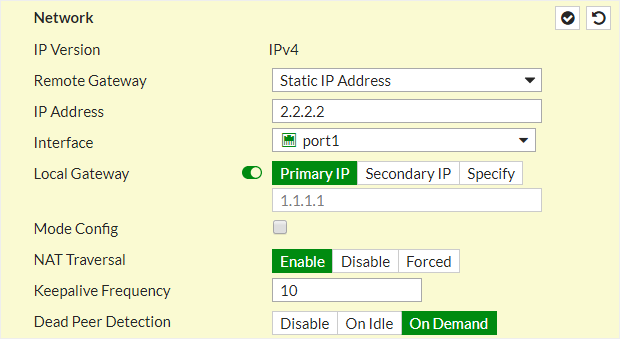
Scroll down the page, and in the Authentication field, select the authentication method Pre-Shared Key and Provide the same key as in SonicWall Firewall. Select the IKE version 1 and Mode as Main (ID Protection).
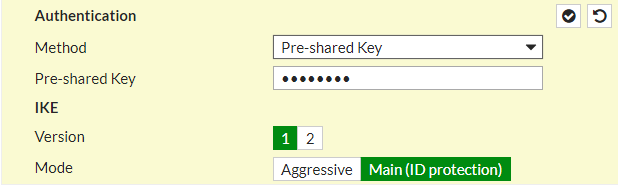
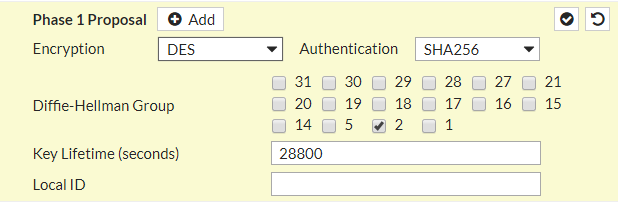
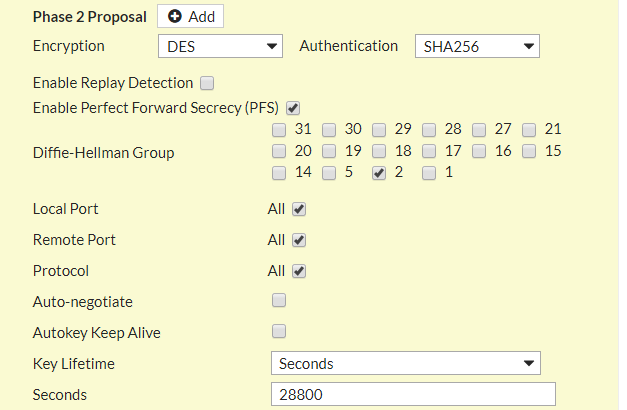
Now, you need to configure the IPSec tunnel Phase 1. As in SonicWall Firewall configuration, we use DES, SHA256, and Group 2 for Encryption, Authentication, and DH Group field. You need to configure the same parameters here as shown in the screenshot.
Key Lifetime must be same as SonicWall Firewwall IPSec Configuration!
After configuring the Phase 1 of IPSec tunnel, now you need to configure Phase 2 as well. Scroll down the Page and edit Phase 2 Selectors. In Local Address and Remote Address fields, you need to define the subnets/ IP address you want to access from this VPN tunnel. In my scenario, I just want connectivity between both LANs. So, In Local Subnet, my LAN subnet will be 192.168.2.0/24 and in Remote Subnet, my remote subnet will be 192.168.1.0/24.
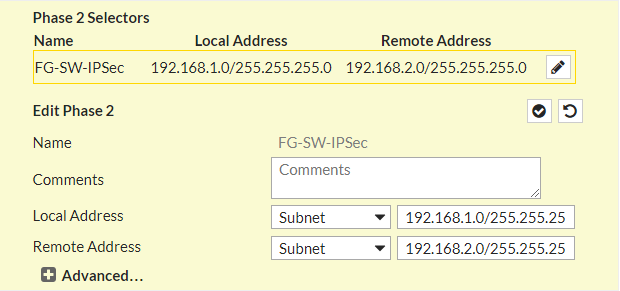
Now, you need to click on (+)Advanced… and configure the Encryption, Authentication, DH Group and Key Lifetime for Phase 2 of IPsec tunnel. These parameters must be the same as SonicWall firewall Phase 2.
Congratulations! We have successfully configured the IPSec tunnel in the FortiGate firewall. Now, you need to create Security Policy and Route for this VPN tunnel.
Configuring Static Route for IPSec Tunnel
Now, you need to add a static route for the remote subnet in the FortiGate firewall routing table, so that traffic can be sent and receive through this tunnel. Access the Network >> Static Route >> Create New. Just define the remote subnet 192.168.2.0/24 to the destination field and select the Tunnel Interface in Interface filed.
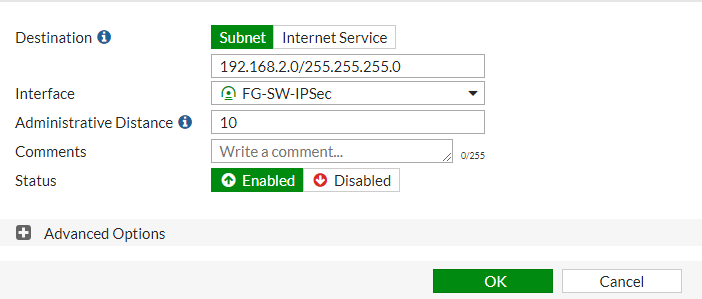
Configuring the Security Policy for IPSec Tunnel
Access the Policy & Objects >> IPv4 Policy >> Create New. Select the Incoming Interface to the tunnel interface and Outgoing Interface to LAN Interface. Allow the traffic you want to access from this tunnel. In this example, I set Source, Destination, and Service to ALL.
For bi-directional communication, we configured two policies.
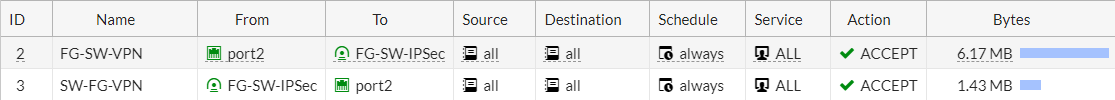
Congratulations! We have successfully configured the IPSec tunnel between the FortiGate & SonicWall Firewall.
Verify the IPSec tunnel on Both FortiGate and SonicWall Firewall
Here, we will verify our configuration by initiating traffic from SonicWall LAN Subnet to Palo Alto LAN Subnet. But, first, we need to make sure that our tunnel is up and in running state.
If you found that the IPSec tunnel is still down. You need to go to the SonicWall Firewall and navigate to VPN >> Settings >> VPN Policies >> Enable/Disable the IPSec tunnel you just created.
Alternatively, In FortiGate Firewall, you can navigate to Monitor >> IPSec Tunnel >> select the tunnel and choose to Bring Up the tunnel.
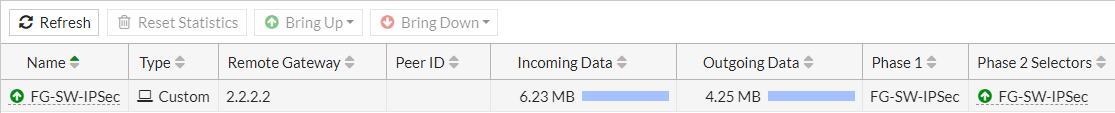
Once the tunnel is up, you can find that both firewalls will show that the IPSec tunnel is Up. Login to SonicWall Firewall and navigate VPN >> Settings >> VPN Policies. You will find that the IPSec tunnel with FortiGate is up.
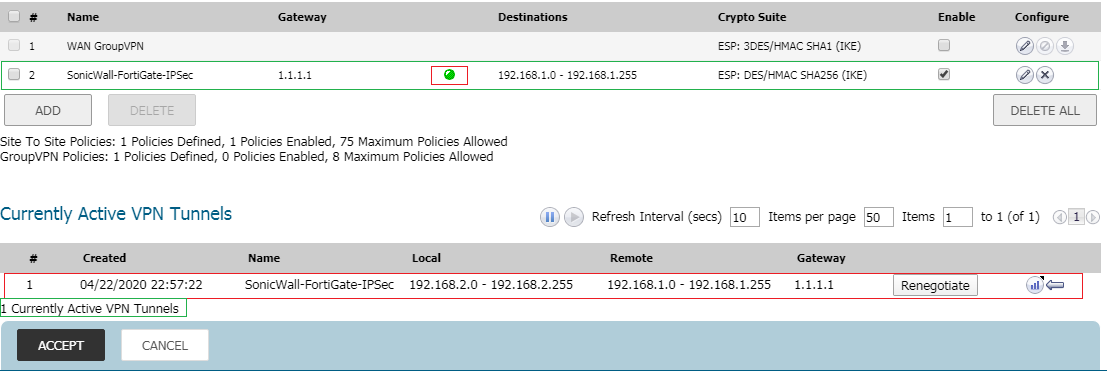
If you are on FortiGate, login to the Firewall. Navigate to Monitor >> IPSec Monitor. You will find that the IPSec tunnel with the SonicWall firewall is up.
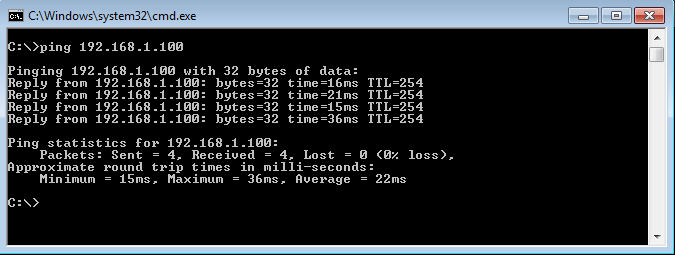
Now, we will initiate ICMP traffic from SonicWall LAN to FortiGate LAN. You will find that we get a response from the FortiGate LAN appliance.
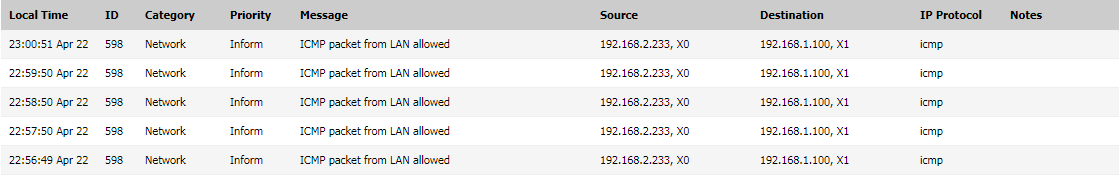
In SonicWall firewall, navigate to Logs and you will traffic logs for the same IPSec tunnel.
That’s it! We successfully configured the IPSec tunnel!
References
Related Articles
- How to configure IPSec Tunnel between Palo Alto and SonicWall Firewall
- How to configure IPSec VPN between Palo Alto and FortiGate Firewall
Summary
In this article, we explained & configure the IPSec tunnel between the FortiGate & SonicWall Firewall. IPSec tunnel, i.e., Site to Site VPN, allows you to connect two different sites. You must have IPSec tunnel supported appliances to create an IPsec tunnel. In this article, we used Pre-Shared Key as the authentication method, however, you can also use certificates. We can use a variety of Encryption and Authentication methods. First, we configured IPSec VPN on SonicWall Firewall, later, we configure it on FortiGate. As you also noticed, SonicWall Firewall creates a security rule itself for IPSec VPN. However, for the bi-directional traffic, we configured an additional rule on the SonicWall firewall. Finally, we initiate the traffic over the IPSec tunnel and check similar logs on SonicWall Firewall.
Did you found this article helpful? Please share this article on social media and shows us some love 🙂
Doesnt appear to work on 6.4.2. Followed tutorial settings, but 6.4.2 has additional settings. Look elsewhere if you’re running this version and need to setup a VPN.
This is for a site-to-site tunnel which is a policy-based VPN. We are using route-based VPN’s which is a tunnel interface on the SonicWall. This doesn’t have/use the network tab on the VPN.
The benefit of this is that the tunnel being up/down is independent of the networks on either side. We have problems with system engineers troubleshooting and not understanding that without network traffic a policy-based VPN can be down when there is no problem with connectivity.